Creating Custom Virtual Firewalls
You can create a custom Virtual Firewall (VFW), which is a virtual machine on the edge of your Cloudspace's network. Custom VFWs make it possible to apply customized firewall configurations and specific routing policies.
Overview
This tutorial first covers how different types of cloudspaces connect to the Internet (or any external network), then it explains what are Custom VFWs and the reasoning behind using such VFWs. Furthermore, we explore how to set up and configure two widely used VFWs (IPFire and pfSense).
Cloudspace Network Overview
A Cloudspace is a logical grouping of cloud resources (e.g., virtual machines, disks) such that these cloud resources share the same internal virtual network subnet.
On creating your Cloudspace, the settings you configure will determine the type of your Cloudspace:
- Public
- Private
- Nested
To find out more about Cloudspaces, see cloudspaces section within the concepts documentation, and the cloudspace detailed documentation.
How do public cloudspaces connect to external networks like the internet?
- On creating a Public Cloudspace, your Cloudspace is assigned a public internet routable IP address where devices on the Internet can connect to your Cloudspace through this address.
- Public Cloudspaces use the built-in VFW that supports basic functionalities such as
- Port Forwards
- Acts as the default gateway for virtual machines inside the cloudspace
- Handing out IP addresses to virtual machines via DHCP
- Reverse Proxies
- Load Balancing
- Connecting to remote Cloudspaces. For your VFW to support more specific behavior, you can instead create a custom VFW which we will get into details later.
- You can expose cloud resources such as virtual machines by creating Port Forwards. The port forward will redirect communication requests from the external cloudspace IP address and specified port number, to the virtual machine and port you specify. See how to create port forwards in cloudspaces.
What are the differences between Private Cloudspaces and Public Cloudspaces ?
Private Cloudspace is isolated from the outside world; it does not have public Internet routable IP address. Private Cloudspaces do not provide port forwards nor a default gateway for the virtual machines inside the Cloudspace.
How does Nested Cloudspace connect to the internet?
Nested Cloudspace is similar to a Public Cloudspace except that the "public" interface of its virtual firewall is in the private network of its parent cloudspace and not publicly exposed to the internet.
How can I route traffic to virtual machines in a Private Cloudspace?
- Routing to virtual machines inside a Private Cloudspace can be done by creating a custom VFW. Custom VFW is your own virtual machine that performs the routing between the external network and your virtual machines.
- You can set up the custom VFW while you are creating your cloudspace or you could do it manually after creating a private cloudspace.
Routing to VMs in a private cloudspace is not done automatically, you will need to configure your custom VFW to route data to the virtual machines. The configuration process is specific to the VFW operating system.
About Custom Virtual Firewalls
- You can create a custom VFW to do the routing between the external network (such as the internet or another cloudspace) and the virtual machines in your Cloudspace.
- The custom VFW is set as the default gateway of the private Cloudspace, it also acts as a firewall and forwards traffic from the outside to the virtual machines in the cloudspace.
- Creating a custom VFW allows you to use your preferred VFW by selecting the VFW image from the list of available images. This also offers the flexibility to configure the disk size, memory and virtual CPUs on your VFW.
- You can access the custom VFW details page like any other virtual machine in your Cloudspace.
Examples
IPFire
Creating a VFW with IPFire
IPFire is a dedicated firewall with many functionalities such as it being a stateful inspection firewall, it can also work as a VPN gateway and it can analyze data packets with its Intrusion Prevention System. To dive deeper into IPFire, check the IPFire Docs.
To create a custom VFW with IPFire
- Perform the steps for creating a public cloudspace by connecting to an external network. On selecting the VFW, follow the following steps to create a custom VFW.
- After you select to create a public cloudspace, select the Using a custom VFW that you choose and configure yourself option.
- On the next page, set up the basic configurations. For the image, select one of the IPFire images such as IPFire.
- Determine the disk size, vCPUs and memory for your VFW. For the purpose of a VFW, we recommend a disk size of 10 GB, with a minimum of 4 GB, 1 GB of memory and one virtual CPU should be sufficient.
Finish creating the cloudspace and you will have a cloudspace with one virtual machine which is your custom VFW.
Managing IPFire VFW in cloudspaces
There are two ways to access IPFire configurations
- Access through the VFW console
- Setting up a management station in your cloudspace using the IPFire Web Interface
To manage the VFW from the VFW Console
- Navigate to your cloudspace details page and select the VFW machine from the listed virtual machines.
- The VFW machine details page will appear. Select CONSOLE from the top of the page. The console window will appear asking you to Log in.
- Log in with the following credentials: "root" as your username, and the password in the Initial Password field located in the VFW details page in whitesky.cloud BV portal.
After typing the password correctly, you will be logged in as "root" and you can configure IPFire.
To manage the VFW from the IPFire Web Interface
- First, you will need to create another virtual machine inside your cloudspace to act as a management station. For a step-by-step guide on creating VMs, see virtual machines documentation. To have access to a GUI, create a virtual machine from an image such as "Ubuntu Desktop".
- Navigate to your newly created virtual machine's details page and select CONSOLE from the top of the page.
- Inside the VM console, Open a browser and enter the URL
https://<VFW-IP-ADDRESS>:444. You can find the VFW IP address from the VFW details page in whitesky.cloud BV portal. - When prompted for the username and password, enter
adminas your username and the password in the Initial Password field located in the VFW details page in whitesky.cloud BV portal.
You will now have access to the IPFire web user interface, where you can access all the settings and perform any installations/configurations for your VFW.
Configure Port Forwarding In IPFire
To expose a web server on one of your virtual machines in your Cloudspace, you will need to create a rule in IPFire VFW.
To add a new Firewall rule in IPFire
- log in to the IPFire web interface. From the top menu, select Firewall Rules from Firewall.
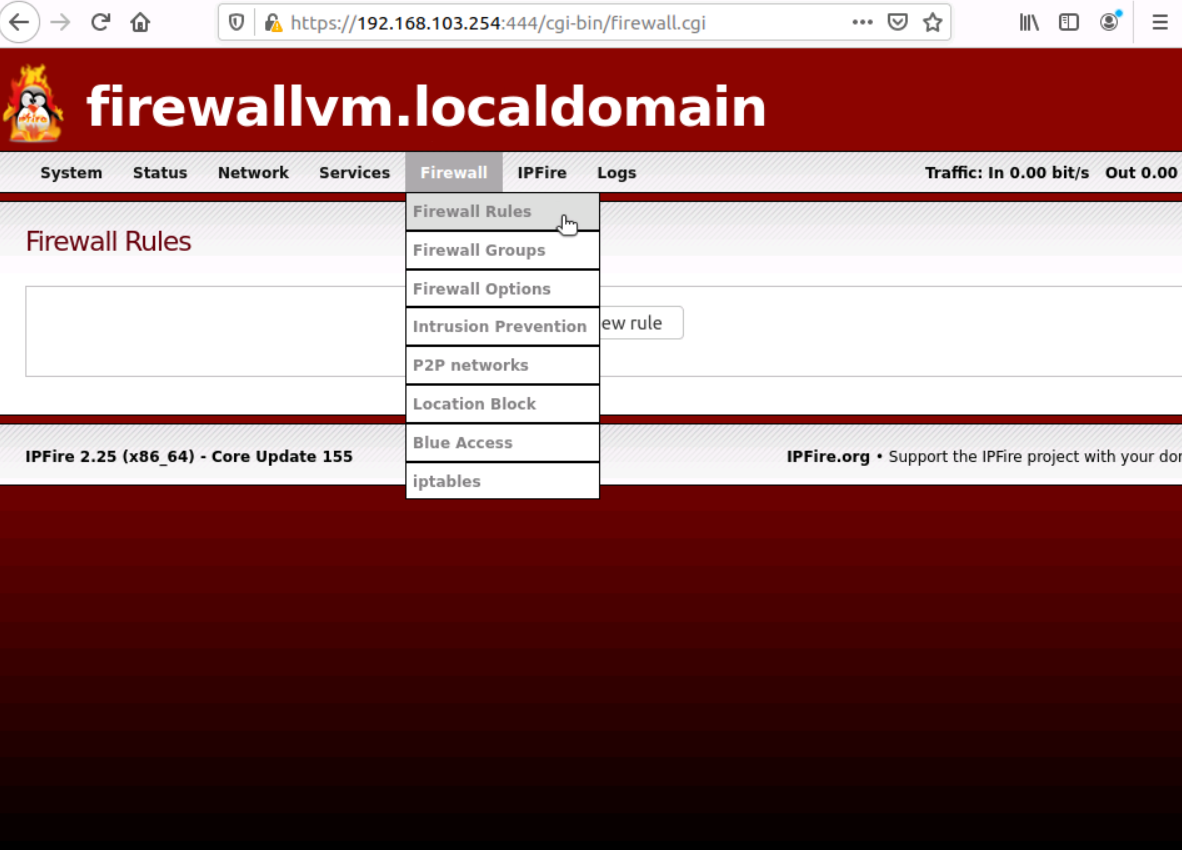
- Click New rule, which will take you to a new Firewall Rules screen.
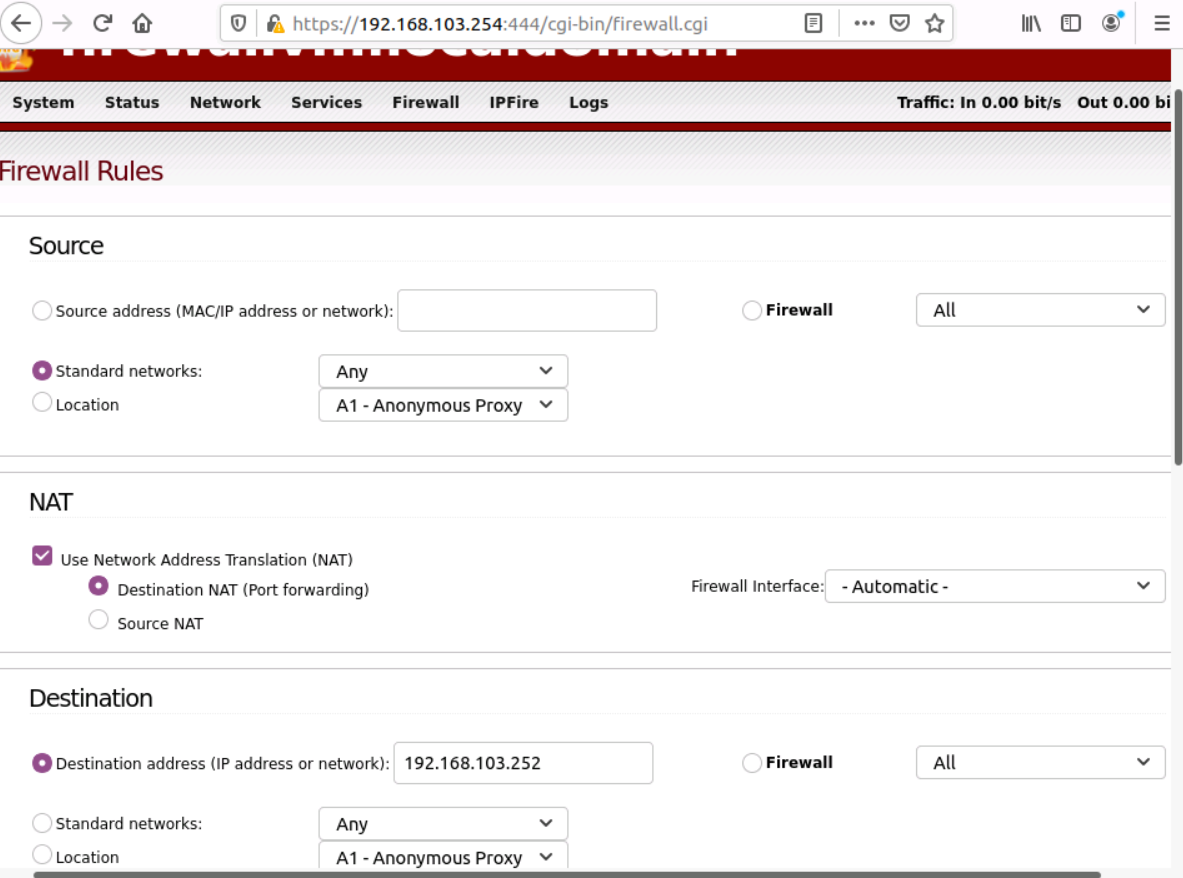
- In the Source section, select the radio button for Standard networks and select Any in the drop-down menu.
- In the NAT section, select the checkbox for Use Network Address Translation (NAT).
- In the Destination section, enter the private IP address for your virtual machine in Destination address (IP address or network).
- In the Protocol section, select TCP in the drop-down menu, and set the port value in the Destination port e.g. 80 for web servers.
- In the Additional settings section, you can add a remark for this rule to explain its purpose.
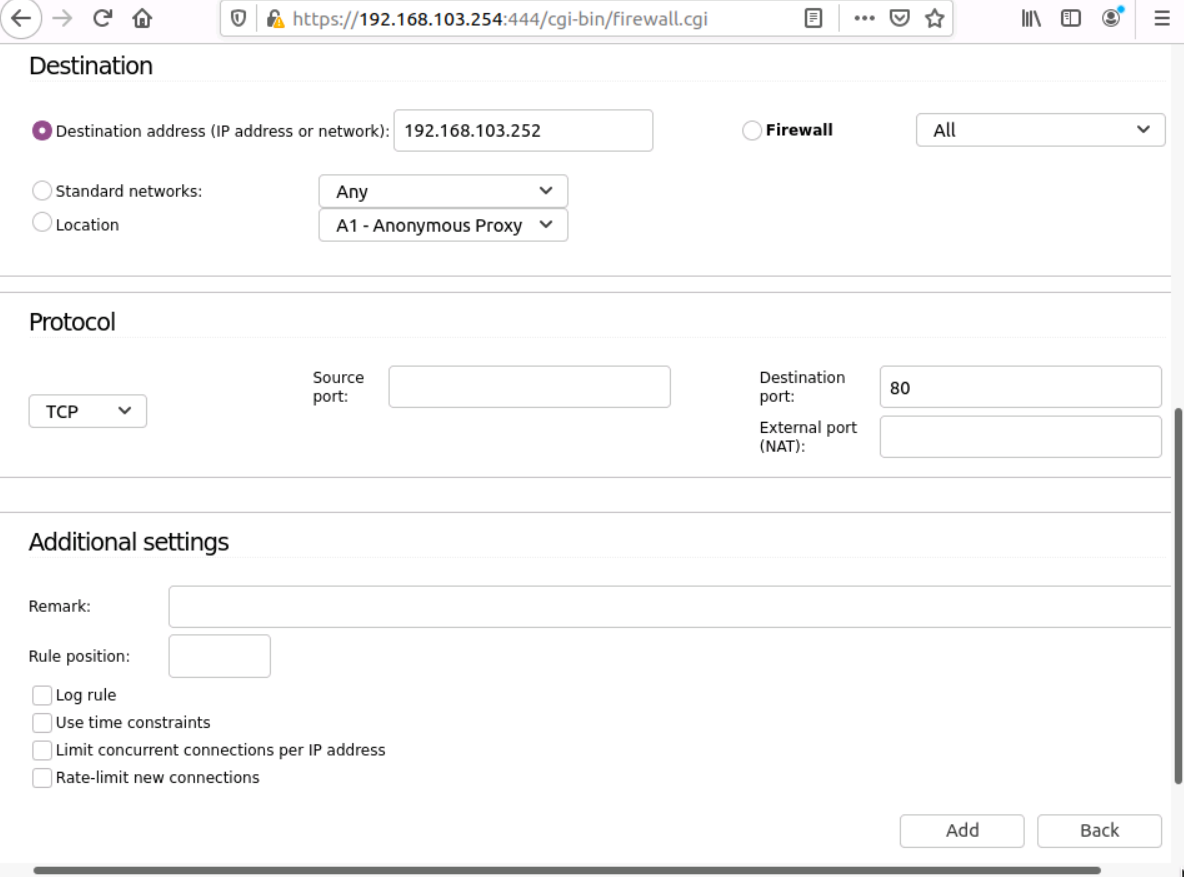
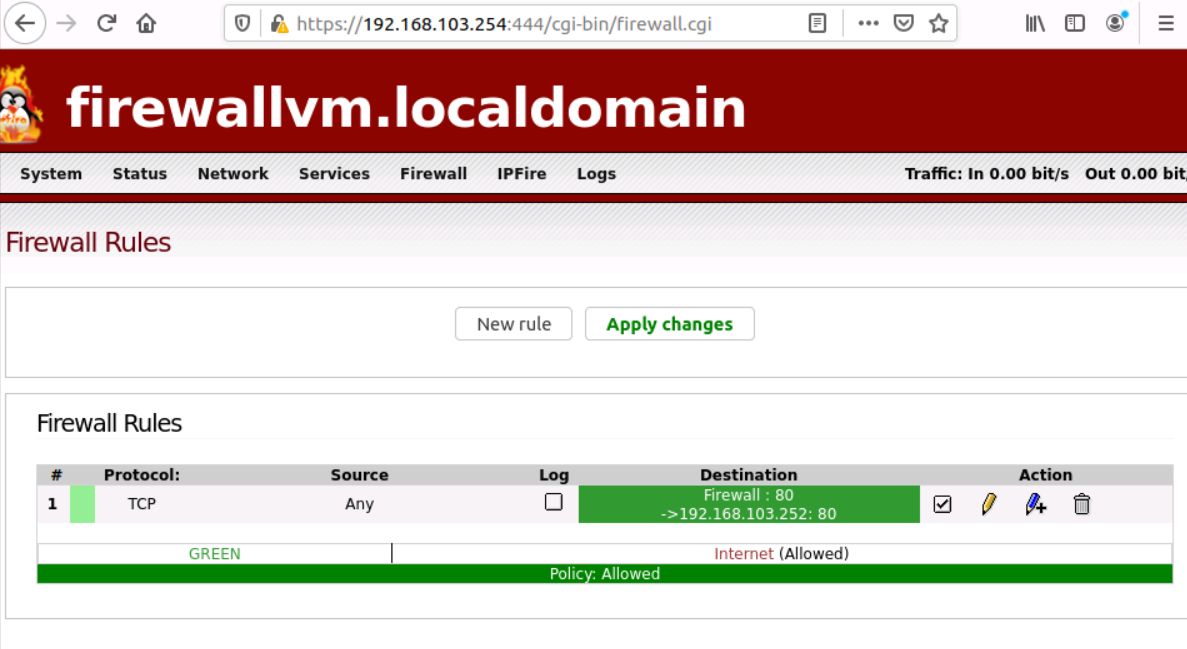
- Click Add at the bottom of the page. A page with the new rule will appear, to finalize this new rule, click Apply Changes. Now the new rule is set in the IPFire VFW.
pfSense
Creating a VFW with pfSense
pfSense is a powerful, flexible firewalling and routing platform with many features. To dive deeper into pfSense, check the pfSense Docs.
To create a custom VFW with pfSense
- Perform the steps for creating a public cloudspace by connecting to an external network. On selecting the VFW, follow the following steps to create a custom VFW.
- After you select to create a public cloudspace, select the "Using a custom VFW that you choose and configure yourself" option.
- On the next page, set up the basic configurations. For the image, select one of the pfSense CDROMs.
- Next, determine the disk size, vCPUs and memory for your VFW.
Finish creating the cloudspace and you will have a cloudspace with one virtual machine which is your custom VFW.
Setting up pfSense VFW from console
To set up the pfSense VFW
- Inside your cloudspace, open the pfSense VFW console. Wait for the pfSense welcome page to load, and hit enter to boot.
- Accept the copyright and distribution notice. The pfSense installer page will appear, select Install from the menu.
- Select the default keymap selection and the disk partitioning you would like, then wait for the installation process to complete. For manual configurations, select No unless you need to configure something manually.
- A message should appear indicating that the installation of pfSense has been completed. Select Reboot to reboot into the installed system.
-
For the system to boot on the hard disk, you should either detach the CD-ROM image from the pfSense VFW in whitesky.cloud BV portal or select to boot from the hard disk by accessing the boot menu. To detach the CD-ROM image
-
Go to the pfSense VFW details page in whitesky.cloud BV portal, select the CDROM IMAGES tab, then select the pfSense image.
-
At the top of the page, click on DETACH FROM FIREWALL_VM.
Another way to boot on the disk would be by accessing the boot menu. At the start of booting the system, you can press F12 for the boot menu, and then select the hard disk (e.g. Virtio disk).
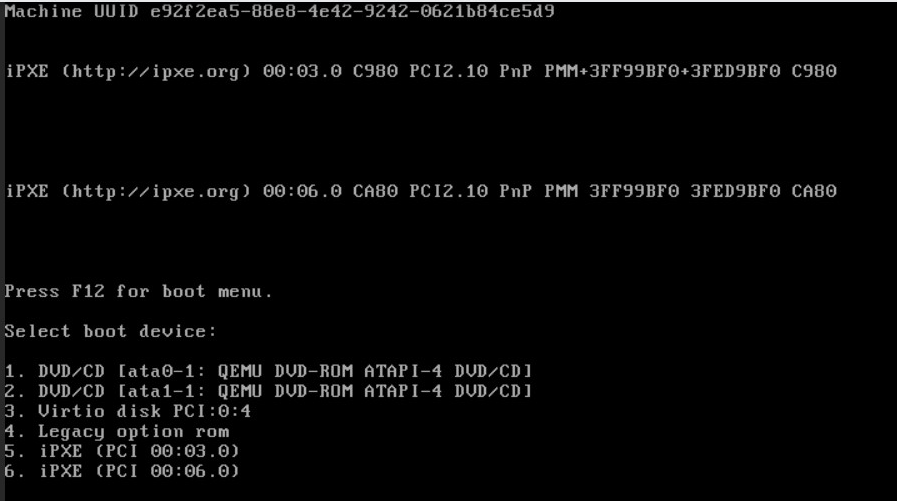
-
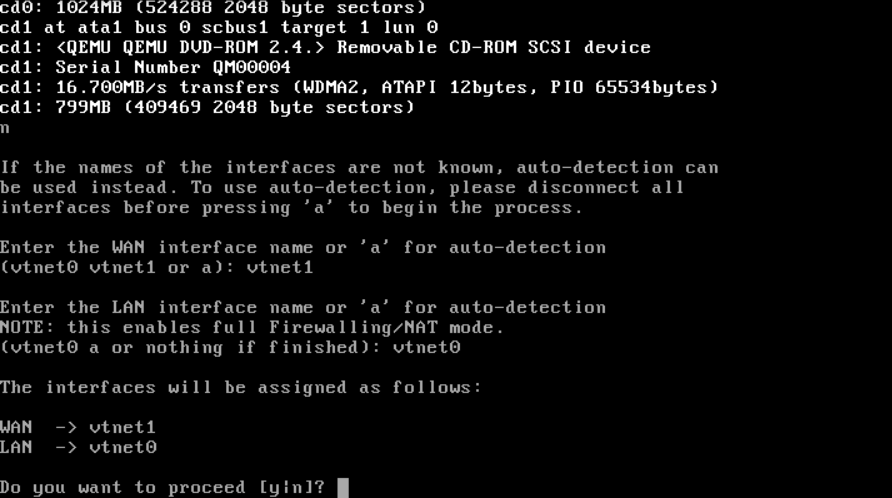
For "Do VLANs need to be set up first?" enter n. We do not use VLANs. Enter the WAN and LAN interface names respectively, in this case it's vtnet1 for WAN and vtnet0 for LAN. Then, enter y to proceed.
- On successful installation and booting, you should see the pfSense menu.
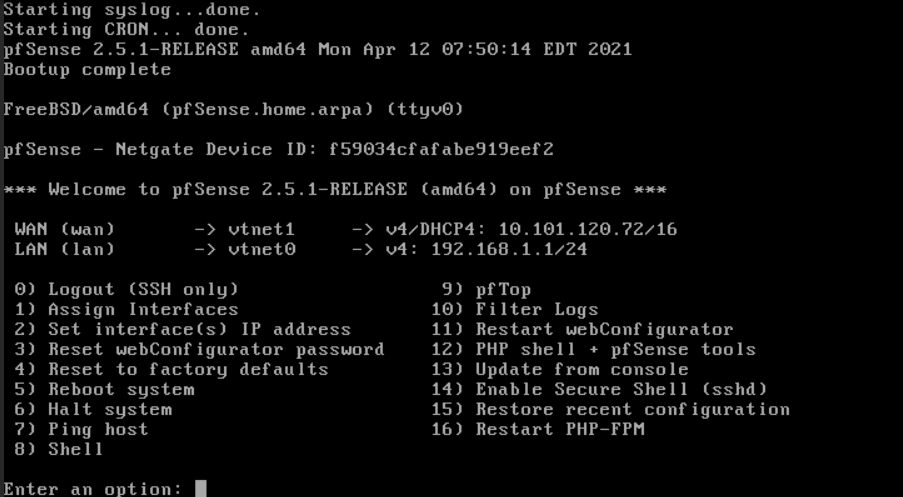
Setting interface IP address in pfSense console
To set the interfaces IP address in the pfSense console
- Enter 2 for Set Interface(s) IP address, where a list of the available interfaces will appear.
- Select the WAN interface. Enter n for Configure IPv4 address WAN interface via DHCP? as we will assign the WAN IP address statically.
- Enter the new WAN IPv4 address, e.g.
10.101.120.72/16Press enter, then enter the new WAN IPv4 gateway address e.g.10.101.0.1.You can find the network information in the pfSense VFW details page in whitesky.cloud BV portal under the NETWORK INTERFACES tab. Click the link under the details field for the network of your choice in order to find the Gateway IP address.
- Enter n for Configure IPv6 address WAN interface via DHCP. Then, press enter to skip the WAN IPv6 address. Enter y to revert to HTTP as the webConfigurator protocol. Finally, press enter to continue.
- Repeat the process to configure the LAN interface. Enter 2 for Set Interface(s) IP address and select the LAN interface. For the LAN IPv4 address, enter the pfSense VFW IP address, which you can find in the pfSense VFW details page in whitesky.cloud BV portal (e.g.
192.168.103.254/24). Press enter to skip the new LAN IPv4 upstream gateway address, the new LAN IPv6 address, and enter n for enabling the DHCP server on LAN.
The WAN and LAN interfaces are now set, and the webConfigurator URL should be displayed.
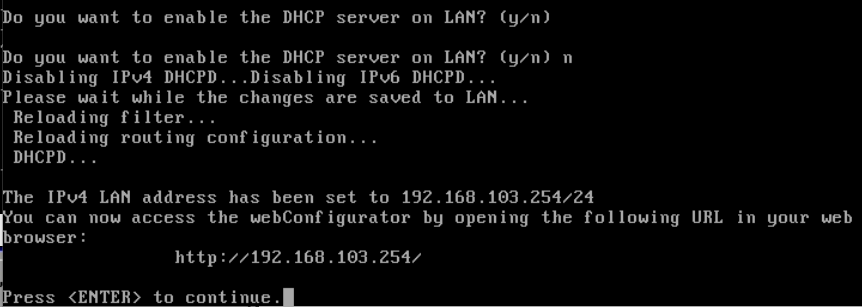
Accessing the pfSense Web Interface
To manage the VFW from the pfSense Web Interface
- You will need to create another virtual machine inside your cloudspace to act as a management station. For a step-by-step guide on creating VMs, see Virtual Machines. To have access to the VFW GUI, create a virtual machine from an image that has a graphical user interface such as a "Windows" or an "Ubuntu Desktop".
- Navigate to your newly created virtual machine's details page and select CONSOLE from the top of the page.
- Inside the VM console, open a browser and enter the URL
http://<VFW-IP-ADDRESS>. You can find the VFW IP address from the VFW details page in whitesky.cloud BV portal. - Log in with the default credentials, username: "admin" and password: "pfSense". Since this is your first time to log in, the pfSense wizard will appear.
- Click Next, until you reach the General Information page. Here you can change the hostname and DNS configuration.
- Select your Time server hostname and Timezone.
- Configure the WAN Interface and other general configurations, you can skip this step since we already configured the IP addresses in the pfSense console.
- Configure the LAN interface, which you can skip too.
- Change the default pfSense admin password and click Next.
- Click reload to reload the pfSense configurations.
Wait for the system to reload, then click finish. The pfSense VFW installation is now complete!
Configure Port Forwarding In pfSense
To expose services from VMs in your cloudspace, you need to add port forwards in the pfSense VFW.
Before creating the port forward, you must know the service's port number and the IP address of the VM running the service.
To create the NAT rule in the pfSense web interface
- Select NAT from the Firewall tab in the top menu, then click Add to add a new rule.
- Select the protocol in the protocol drop-down box e.g. (TCP, UDP..)
- In the Destination Port Range enter the port number e.g (80 for HTTP) in the from box. You can leave the to box empty if you are forwarding to a single port.
- In the Redirect target IP box, enter the VM's IP address e.g.
192.168.103.252. In the Redirect target port, enter the port number again.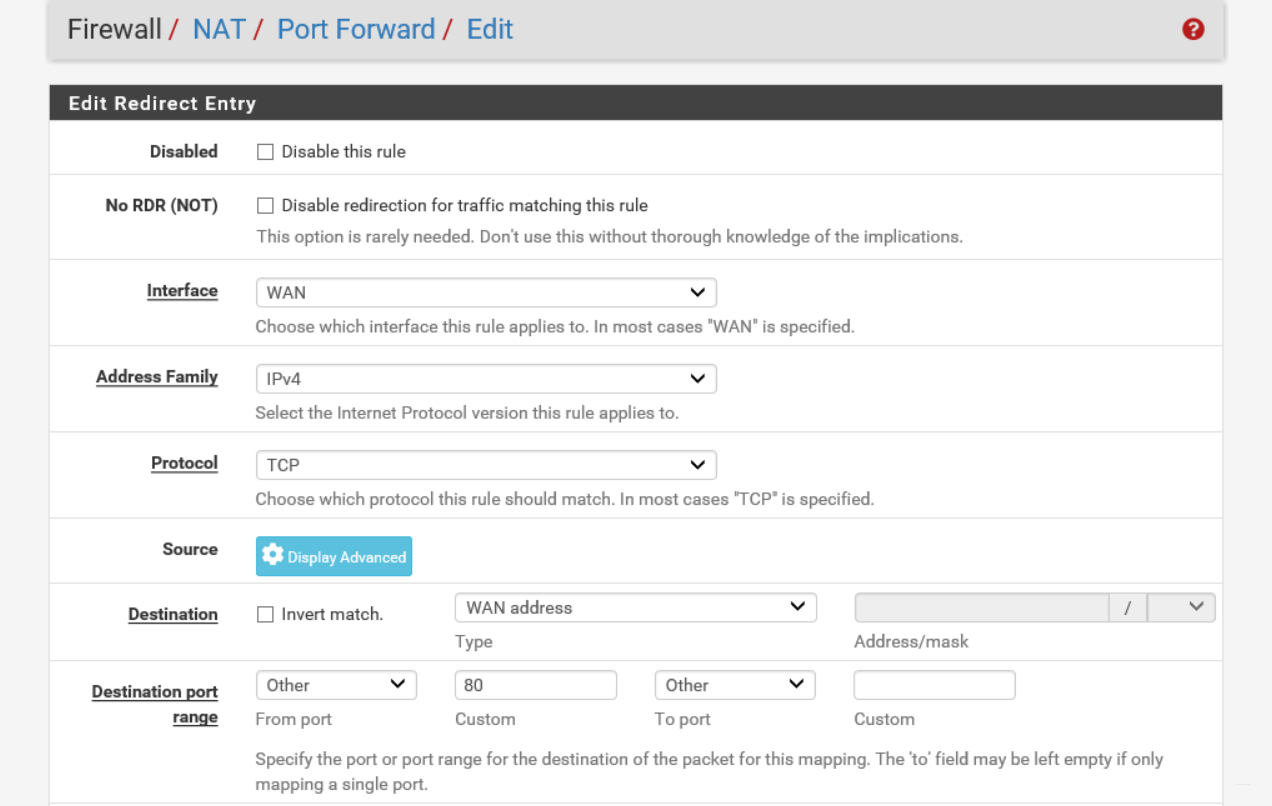
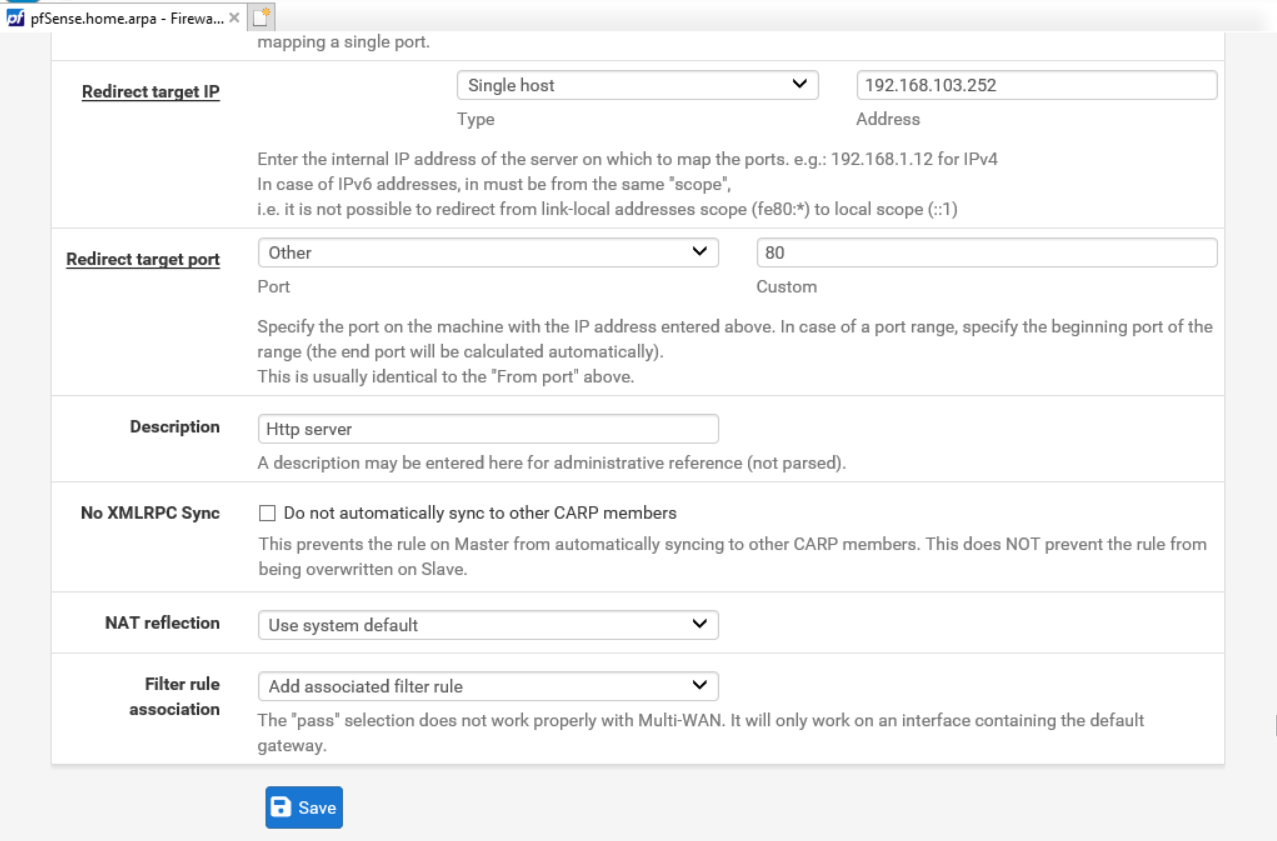
- Click Save, then Apply Changes.
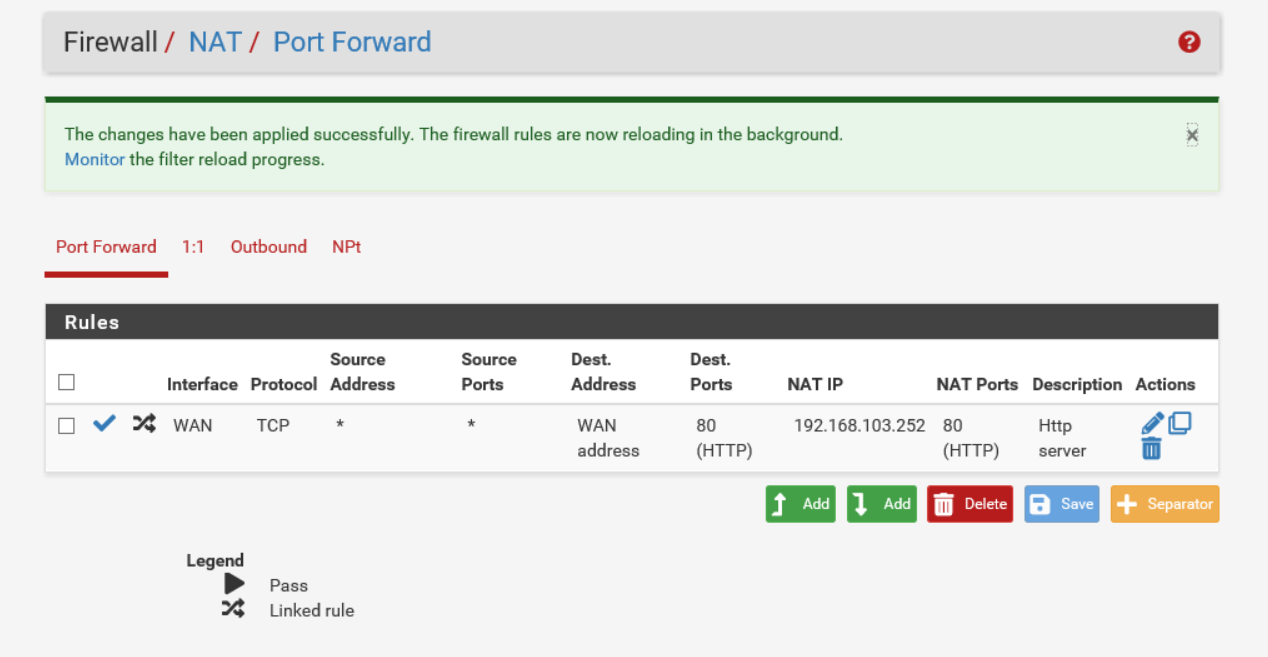
The new rule will be applied and added to the Rules table.